On March 16, FortiGuard Labs captured a new Word file that spreads malware by executing malicious VBA (Visual Basic for Applications) code. The sample targeted both Apple Mac OS X and Microsoft Windows systems. We then analyzed the sample, and in this blog we are going to explain how it works, step by step.
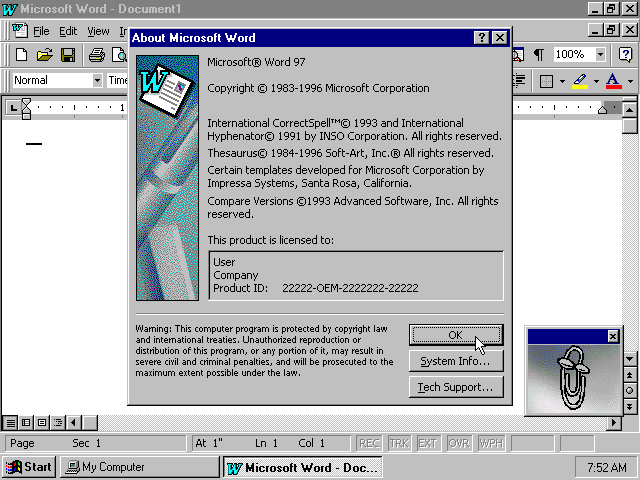
When the Word file is opened, it shows notifies victims to enable the Macro security option, which allows the malicious VBA code to be executed.
The 'classic' Mac OS is the original Macintosh operating system that was introduced in 1984 alongside the first Macintosh and remained in primary use on Macs until the introduction of Mac OS X in 2001. Apple released the original Macintosh on January 24, 1984; its early system software was partially based on the Lisa OS and the Xerox PARC Alto computer, which former Apple CEO Steve Jobs. The word completion feature in Mac OS X » Learning » 4All » Tech Ease: The word completion feature can be helpful when you start typing a word and can’t remember the exact spelling. Start quickly with the most recent versions of Word, Excel, PowerPoint, Outlook, OneNote and OneDrive —combining the familiarity of Office and the unique Mac features you love. Work online or offline, on your own or with others in real time—whatever works for what you’re doing. Download Mac software in the Word Processing category. Navigate the web while avoiding intrusive ads and trackers, support your favorite websites in new ways, and even make money by viewing private ads, all with this innovative Chromium-based browser. If it prints successfully that tells us that the problem is in your existing document. See Troubleshoot damaged documents in Word for Mac. If it doesn't print successfully try changing the font of your text by selecting your sample text, choosing the Font drop down on.
Malicious Word File is Opened
Figure 1. Asks victim to enable Macro security option
Once the malicious VBA code is executed, the AutoOpen() function is automatically called. The first thing it does is read the data from the “Comments” property of the Word file.
Figure 2. The property “Comment” of the Word file
The value of the “Comments” is base64 encoded, which can be read out and decoded by the VBA code below:
After it’s base64-decoded, we can capture the code in plaintext, which is python script, as shown below.
Next, it takes a different route depending on the OS type, Apple Mac OS X or Microsoft Windows, that it is running on. You can see this in the the flow chart in Figure 3.
Figure 3. Calling different route according to OS type
We have found that this malicious VBA code uses slightly modified code taken from a metasploit framework which you can find at hxxps://github.com/rapid7/metasploit-framework/blob/master/external/source/exploits/office_word_macro/macro.vba
How it Works for Apple Mac OS X
As you probably know, Mac OS X comes with Python pre-installed by Apple. This allows it to execute python scripts by default. As you can see above, the base64-decoded python script is passed to the ExecuteForOSX function that is going to execute it at the bottom of the function (see Figure 3).
The python script is easy to understand. It extracts the code from a base64-encoded string, and then executes it. It is decoded below, and as you can see, it is a very clear python script.
When the python script is executed, it downloads a file from “hxxps://sushi.vvlxpress.com:443/HA1QE”, and executes it. The downloaded python script is a slightly modified version of the Python meterpreter file, which is also part of the Metasploit framework. The source code of the project can be downloaded from the following URL: hxxps://github.com/rapid7/metasploit-payloads/blob/master/python/meterpreter/meterpreter.py.
The major changes between the downloaded file (HA1QE) and the original file are the following:
Figure 4. Differences between HA1QE and meterpreter.py
The HTTP_CONNECTION_URL constant (hxxps://sushi.vvlxpress.com:443/TtxCTzF1Q2gqND8gcvg-cwGEk5tPhorXkzS0gXv9-zFqsvVHxi-1804lm2zGUE31cs/) is set to the Metasploit end-point that the script will be connecting to.
The PAYLOAD_UUID constant is used as an identifier for the client, which we believe is also being used by the attackers for campaign-tracking purposes.
Once the script is executed, it attempts to connect to the host “sushi.vvlxpress.com” on port 443. But at the time the request was made during our analysis, the listener (server) was not answering client requests.
Figure 5. Wireshark showing TCP retransmission error while connecting to the server
The python process remains active on the system while trying to connect to a reachable server.
Figure 6. Python script attempting connection to listener
How it Works for Microsoft Windows
Although the argument of the ExecuteForWindows function is as same as the ExecuteForOSX function, it does not use it. What it does instead is making a DOS-style command string starting with cmd.exe. When it is executed, powershell.exe is started without window (-w hidden), and it executes the base64-encoded code (-e base64-encoded code.) For more details, see the following screenshot.
Figure 7. Dos-style command

It’s base64 again. This malware’s author likes using base64 to encode the sensitive code. We will see more base64 encoded data in the rest of the analysis.
Decoding the base64-encoded data, we get the following powershell script:
The main job of the above powershell script is to decompress a piece of gzip data, which is in base64-encoded code, to get another powershell script (by calling FromBase64String() and GzipStream()) and execute it (by calling Start($s)).
Next, let’s move on to see the decompressed powershell code. To improve understanding, I modified some of the function and variable names.
Here is the code snippet:
From the above powershell code we can see that it first decodes the base64-encoded data. In fact, it is 64-bit binary code that is going to be executed later. Then, it allocates a buffer in the current process (powershell.exe) and copies the 64-bit code into the buffer by calling the VirtualAlloc and Copy functions. Finally, it calls the CreateThread function, whose thread function points to the new buffer. That means that the 64 bit code is the thread function and is executed. Based on our analysis, this malware only affects 64-bit Windows.
Figure 8. 64-bit ASM code
We analyzed the 64-bit code in IDA Pro, as shown in the above screenshot. Once it starts, it downloads a file from “hxxps://pizza.vvlxpress.com:443/kH-G5” into a newly allocated buffer. The downloaded file is actually a 64-bit DLL file. Before the thread function finishes, its stack return address is set to the newly allocated buffer that holds the downloaded 64-bit DLL. That means that the 64-bit DLL gets executed when the thread function is returned.
Next, we see that the DLL can communicate with its server, such as “hxxps:// pizza.vvlxpress.com:443/5MTb8oL0ZTfWeNd6jrRhOA1uf-yhSGVG-wS4aJuLawN7dWsXayutfdgjFmFG9zbExdluaHaLvLjjeB02jkts1pq2bR/”. We can see it in the debugger, as shown below.
Figure 9. Communication with its server
At this point, we are still working on analyzing the downloaded DLL and trying to gather more information from it. We’ll share more details about this malware later as we uncover more interesting details.
Mitigation
The original Word sample file has been detected as “WM/Agent.7F67!tr” by FortiGuard AntiVirus service.
IoCs
URL:
hxxps://sushi.vvlxpress.com:443/HA1QE
hxxps://pizza.vvlxpress.com:443/kH-G5
hxxps://pizza.vvlxpress.com:443/5MTb8oL0ZTfWeNd6jrRhOA1uf-yhSGVG-wS4aJuLawN7dWsXayutfdgjFmFG9zbExdluaHaLvLjjeB02jkts1pq2bR/
hxxps://sushi.vvlxpress.com:443/TtxCTzF1Q2gqND8gcvg-cwGEk5tPhorXkzS0gXv9-zFqsvVHxi-1804lm2zGUE31cs/
Sample SHA256:
Sample.doc 06A134A63CCAE0F5654C15601D818EF44FBA578D0FDF325CADFA9B089CF48A74
HA1QE.py 3A0924D55FB3BF3C5F40ADCE0BD281D75E62D0A52D8ADFA05F2084BA37D212C8
kH-G5.dll C36021A2D80077C2118628ED6DB330FEF57D76810FF447EF80D2AB35B95099BC
Sign up for weekly Fortinet FortiGuard Labs Threat Intelligence Briefs and stay on top of the newest emerging threats.
Word For Mac Os X 10.7.5
Also found in: Dictionary, Thesaurus, Medical, Financial, Acronyms, Wikipedia.
Mac OS X
(operating system)Mac OS X
(Mac OS 10) The current operating system from Apple for the Mac family. Starting in the fall of 2016, Version 10.12 uses the rebranded 'macOS' moniker and not OS X. See macOS and Sierra.OS X Server was introduced in 1999, and the client version came out in 2001. Based on Unix and featuring an entirely redesigned user interface, OS X was a major departure from the previous OS 9 system. For the first time, the rich set of Unix commands became available to all Mac developers (A/UX was an earlier Unix OS for the Mac but was not widely used).
OS X added protected memory, pre-emptive multitasking, multithreading and symmetric multiprocessing (SMP) to the Mac world. The heart of OS X is the open source, POSIX-compliant Darwin kernel, which includes an enhanced BSD 4.4 operating system and Mach 2.5 microkernel. See HFS.
Word For Mac Os X 10.11.6
 Legacy Software
Legacy SoftwarePrior to Mac OS X 10.5 (Leopard), OS X ran legacy OS 9 and earlier applications via its Classic software, which was a full copy of OS 9 that ran as an OS X process. Classic was not preloaded on new Macs, but was available for installation from the system disks.
In 2006, Apple switched from the PowerPC to the Intel platform, and Classic support was dropped in the Intel version of OS X. However, PowerPC applications could run on Intel Macs via an emulator (see Rosetta).
Programming Environments

There have been five programming interfaces (APIs) for writing Mac OS X applications. Cocoa is the native OS X interface, derived from OpenStep. Carbon is used for applications that can run on both OS X and earlier Mac OS machines, and Classic is the API prior to Mac OS X. Programs can also be developed in Java and BSD. See OpenStep and Cocoa.
Faster Cats!
Mac OS X versions were internally code-named after jungle cats. Starting with Version 10.2 (Jaguar), the animals became the official product name until Version 10.9 (see below). See Rhapsody and Bonjour.
Want to thank TFD for its existence? Tell a friend about us, add a link to this page, or visit the webmaster's page for free fun content.
Link to this page:

